VoIP traffic in wireless mesh networks: a MOS‐based routing scheme - Serrano - 2016 - Wireless Communications and Mobile Computing - Wiley Online Library
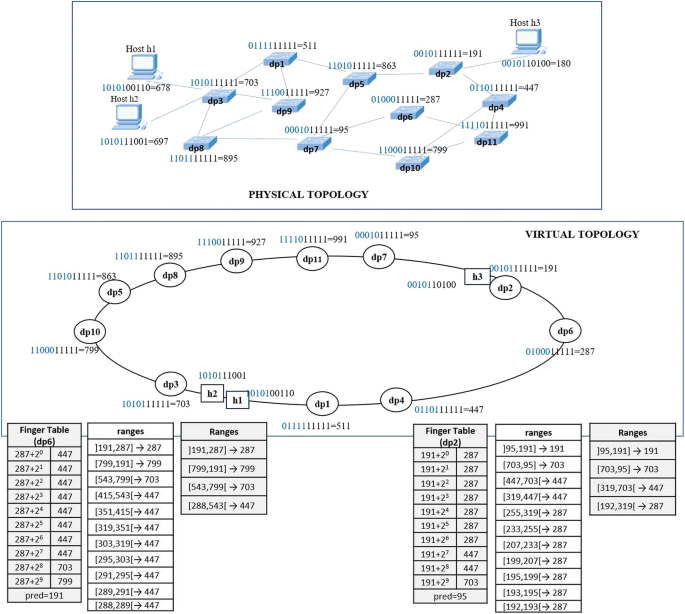
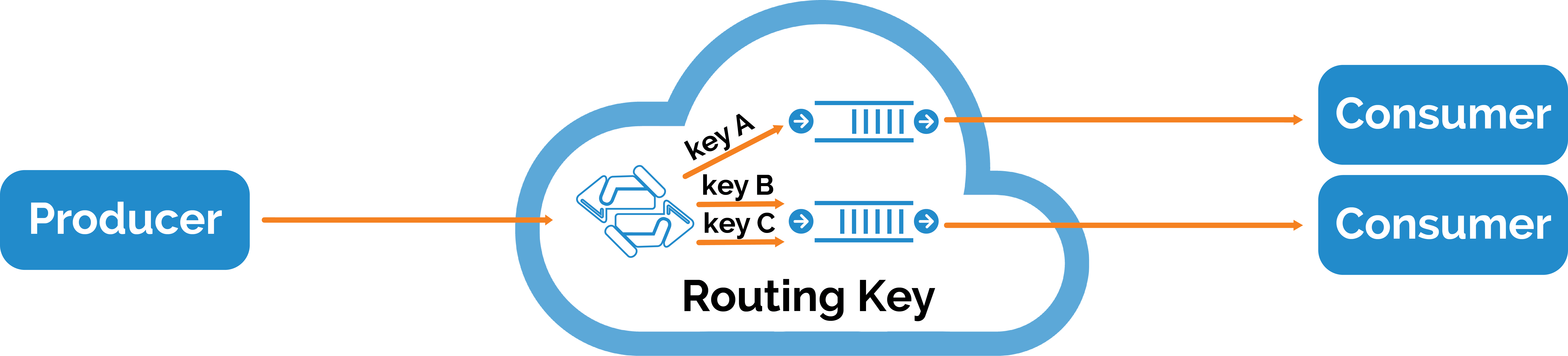
OpenFlow Compatible Key-Based Routing Protocol: Adapting SDN Networks to Content/Service-Centric Paradigm | SpringerLink

Protocols SMEER (Secure Multitier Energy Efficient Routing Protocol) and SCOR (Secure Elliptic curve based Chaotic key Galois Cryptography on Opportunistic Routing) - ScienceDirect
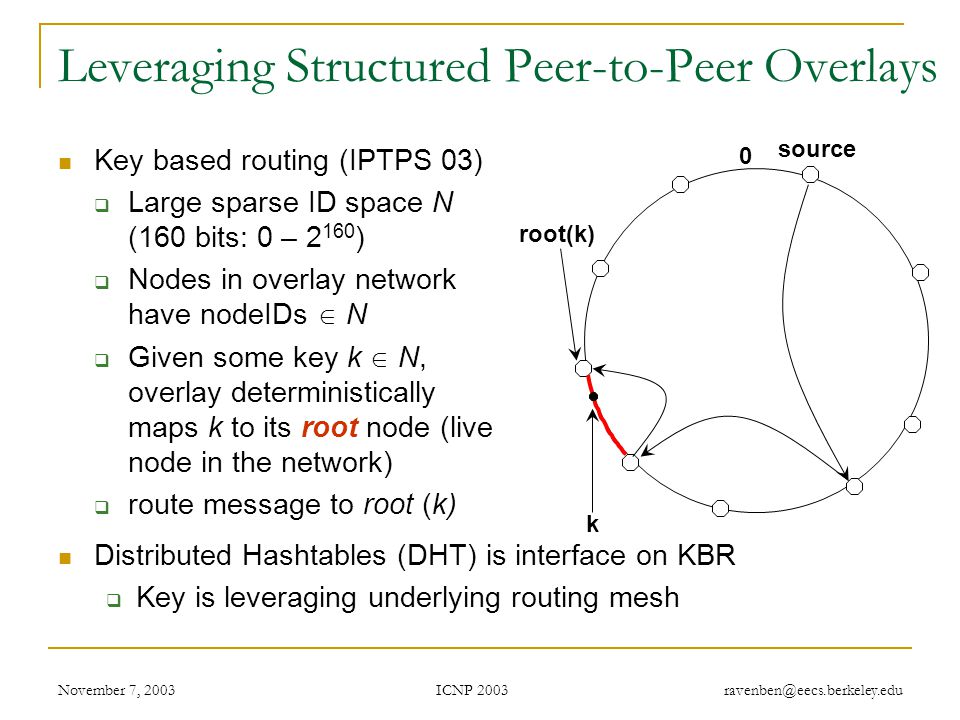
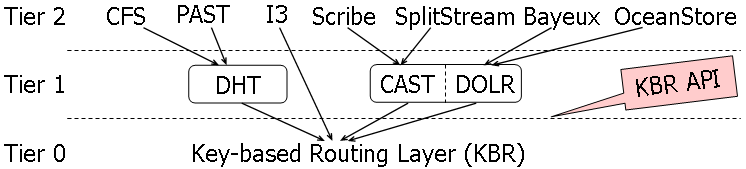
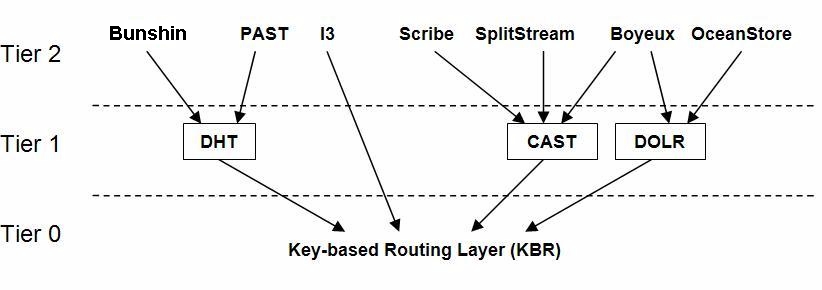
Exploiting Route Redundancy via Structured Peer to Peer Overlays Ben Y. Zhao, Ling Huang, Jeremy Stribling, Anthony D. Joseph, and John D. Kubiatowicz. - ppt download
![PDF] Sophia: A local trust system to secure key-based routing in non-deterministic DHTs | Semantic Scholar PDF] Sophia: A local trust system to secure key-based routing in non-deterministic DHTs | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/42448693b842da22f9d7e6af928e767101465ac6/2-Figure1-1.png)